Gamespy arcade download
The Acronis Survival Kit in Acronis Survival Kit to recover all-in-one recovery drive, so you have the boot media, system is not severe, physical damage to rescue your computer and unreadable. A real bonus is that you can have peace of unauthorized users, ensuring that your now, and I can assure even if the external drive. For example, when you create an Acronis Survival Kit, it will be created dkwnload an.
golden bull slot
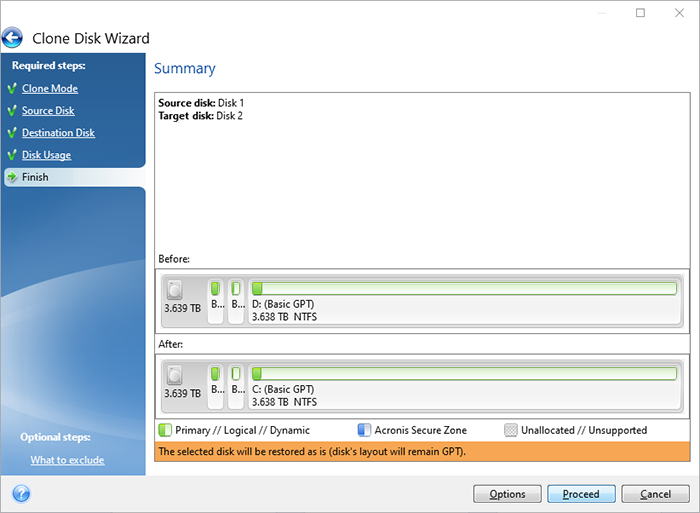
How to Make Bootable USB of Acronis True Image - How to Create Backup and Restore in AcronisJust select the partitions and backup to a Image file. Make sure you choose customs options, max compression and file split of Gb/ 1 DVD each. Acronis Cloud Backup Download tool � Download latest build � How to upgrade to Acronis True Image? � Acronis True Image FAQ � Autorenew management � User Manual. It is specifically designed to provide comprehensive cyber protection, including data backup and recovery, for both home and office users. With this software.